Did you face any of these problems with your notebook? Test -1 This first test will conclude whether your VGA card is in proper function or not. Note that you might still see the flickering. Do not answer" No" just because you see the flickering. Test 2. If you're using a Graphics adapter, like NVidia, G-Force etc. you'll need to run this second test. Simply connect your monitor with an external monitor, and see the display. If you still see flickering, it could be a problem with your Graphics Adapter, and you'll need to get it replaced.
Symptoms
When restarting, the LCD screen would display flickering, vertical, random-like lines in different colors. These lines would appear as soon as the BIOS screen appeared ?
In Windows, you had to disable the video adapter, otherwise the screen would go black. Also, changing the resolution would sometimes cause the system to shut down by itself ?
Sometimes when starting up Windows, the color quality would automatically be set to 4bits (really bad). When changing this to 16 bit, it would sometimes change correctly, and sometimes not?
Screen Flickering Problem: Toshiba, Dell,
Posted by Muhammad | 2:21 AM | Computer Troubleshooting, Hardware Test Utilities, Laptop Troubleshooting, LCD Issues | 1 comments »Imagine if a computer virus emerged that secretly attached itself to one of the most popular software programs ever. Imagine if the largest media outlets unwittingly praised this secret pairing, encouraging millions of people to install it. Imagine if none of the major antivirus programs would detect it. Imagine if once installed, it could alter anything on your computer without your consent or knowledge. Imagine if the virus was at the control of a greedy entity that has repeatedly trampled on consumers and smaller companies to advance its corporate agenda. Imagine if it could force everyone who wanted to communicate with you to also carry the virus so it would insidiously spread person to person. Sound like a scary sci-fi plot? It's not science fiction. This week MO3 will be released on the world. Here's how to detect it in your neighborhood and what you can do to protect yourself
The Trojan Horse
Press outlets will blanket the world with stories about Microsoft Office 2003. Most articles will tout seemingly innocuous features and feel good quotes from Microsoft like "this is our most important product release ever." Unfortunately the press won't talk about the dangerous software buried inside this release - MO3. This code will give Microsoft the ability to change anything on your computer at anytime they wish with no notification to you.
The Security Ploy
Post 9/11, few people question actions taken under the guise of "improved security" and this is how MO3 will be foisted onto computer users - as a feature to 'make you safer.' Computer users have understandably tired of the near daily worm and virus warnings, as well as the time-consuming patch process due to Microsoft's lax software standards and its focusing not on building secure products, but products that secure its monopoly market positions. To improve the predicament which they've created, Microsoft is forcing consumers to accept MO3 embedded into every computer. Listen closely and you'll hear Microsoft mouth pieces speak of "turning software into a service" which really means they will be changing the software on your computer whenever they feel like it. They will slowly limit your ability to run non-Microsoft software. They will restrict choices on your computer to only those products they approve. They will make changes which cripple other software programs or reduce their ability to interoperate with your computer so you will be forced to use exclusively Microsoft approved products.
History Repeats Itself
Microsoft may use this newfound power to fix some holes in their software, but they will also abuse this power to further their corporate monopoly and increase their control and profits. Microsoft has already embedded the MO3 virus into another operating system they have deployed, called Xbox. They now have the power at anytime to change all existing Xboxes which connect to the Internet, and they are already misusing it. They have deleted files from users' computers without their knowledge or permission. They have added software which has removed the ability to run competitor's software. They have been changing users' systems without their consent and notification. They will do the same on Microsoft Windows based computers once MO3 is installed.
Microsoft management has shown to be deceitful and dishonest and will continue this behavior. Twice Microsoft has been found guilty by the Federal government of using illegal tactics to drive competitors out of business and extend their monopoly. December 1st, 2003 a trial will take place in Seattle Washington where more of Microsoft's past behaviors will come to light.
Infecting Friends
Microsoft Word (.doc) file open in StarOffice 7 To stop the advance of competing products and to force users into purchasing new software with the MO3 virus, Microsoft is making certain Microsoft Office 2003 files unreadable by all older versions of Microsoft Office and all competing office suites. Products like Sun's StarOffice are getting extremely good at interoperating with Microsoft word processing, presentation and spreadsheet files making it possible for people to spend close to $50 for an office suite instead of giving $400 or more to Microsoft. To blunt this and force users of older versions of Microsoft Office to buy new software, Microsoft has changed the specifications for some files.
Again under the umbrella of "security," Microsoft is implementing features which limit who can open and edit documents to further thwart competition. Microsoft Office 2003 gives its users the ability to control who can read and edit certain documents, but only if they use the latest Microsoft software. If one user within an office uses this feature, all others will be unable to use any other office suite to access that document. They will not be permitted to run Linux software, they will be required to purchase and run additional copies of Microsoft Office 2003. Since documents are frequently emailed around via the Internet, this will force others to accept Microsoft's software or be unable to communicate. Microsoft refers to this as IRM for "information rights management," but it's really an "infection relay method" designed to force everyone to adopt MO3. They will be using scare tactics about leaked memos or misdirected emails to persuade unwitting computer users to deploy this technology. Doing so will create a viral growth of MO3 which will give MS unlimited power over every computer.
Universal MO3
MO3 will not only come with Microsoft Office 2003, but with future Microsoft products as well. The same technology will be embedded into the next version of Microsoft's operating system software so all users will have to accept it with their new computer. Latest estimates indicate this new software will not ship until 2006, so between now and then, watch for Microsoft to secretly embed MO3 into updates or security patches that they promote for their existing product line.
Protect Yourself
Microsoft Excel (.xls) file open in StarOffice 7 There are precautionary measures you can take to fend off MO3. First off, do not purchase and install Microsoft Office 2003. Also, discourage those around you from purchasing Microsoft Office as well, since one infection will quickly grow. If you need a new office suite, check out the solid and affordable StarOffice 7.0 which runs equally well on Microsoft Windows or Linux computers, and can be purchased online and immediately downloaded and installed. Encourage those penning articles and reviews to fully inform their readers of the dangers of Microsoft Office 2003. Finally, encourage them to do in-depth reviews of Microsoft Office 2003 vs. Sun's StarOffice 7.0 so people can make informed decisions about the benefits and risks of either product.
Broken Screens!!! The worst case scneario
Posted by Muhammad | 12:08 PM | Laptop Troubleshooting, LCD Issues | 0 comments »Laptops are sensitive gadgets. Since we move it around from places to place there are more chances for us to make a stupid mistake to break some thing out of it. Most common part of notebooks which are mostly get the treat is "laptop screen" Laptop LCDs are most attractive and most sensitive part, if it falls or little pressure is exerted over LCD it can break and ruin the the laptop forever. That is understood most of LCD breaking tragidies happens because of accidental fall, but you will not believe that there are many people who braeks LCDS with thumb by applying pressure on screen just to see the liquad and colors of the screen moving inside. Try to avoid this childish act because this action can cost you your laptop.
Worm infections in Laptops/Notebooks
Posted by Muhammad | 9:33 AM | Computer Troubleshooting, Laptop Troubleshooting, Performance Boosting, Top Threats | 0 comments »

 Worm infections spreading through computers, networks, pin drives are reaching in millions due to low profile security measures. In October 2008, different malicious computer programs like conficker, downadup and kido were discovered; these are the most common known malicious software attacking our computers. Antivirus firm F-secure estimated the amount of infected machines have reached the figure of 8-9 million. There has been several warning by experts about this figure that it can go far higher and they should install Microsoft MS08-067 patch and keep anti-virus software updated.
Worm infections spreading through computers, networks, pin drives are reaching in millions due to low profile security measures. In October 2008, different malicious computer programs like conficker, downadup and kido were discovered; these are the most common known malicious software attacking our computers. Antivirus firm F-secure estimated the amount of infected machines have reached the figure of 8-9 million. There has been several warning by experts about this figure that it can go far higher and they should install Microsoft MS08-067 patch and keep anti-virus software updated.
While in Interview with BBC, Graham Cluley, senior technology consultant told that the situation has never been this bad and outbreak on this scale had not been seen for quite some time. He also told that :
"Microsoft did a good job of updating people's home computers, but the virus continues to infect business who have ignored the patch update.
"A shortage of IT staff during the holiday break didn't help and rolling out a patch over a large number of computers isn't easy.
"What's more, if your users are using weak passwords - 12345, QWERTY, etc - then the virus can crack them in short order," he added.
"But as the virus can be spread with USB memory sticks, even having the Windows patch won't keep you safe. You need anti-virus software for that."
How worm spread in windows?
Microsoft has release the information about the working of worm spreading in the windows platform. First of all it searched for executable file called “services.exe” and gets embedded into it. “Services.exe” is windows file which performs important functions in windows. It then copy itself into window system folder “system32” with random file name but in extension of DLL file, it can be something like piftoc.dll etc, it normally named itself from 5 to 8 character, after naming it modifies the registry entries, listing important windows settings so that it could run infected ..DLL file as window default system file. When worm is up and running it creates HTTP server, it resets machine system restore point and starts to download files from different hacking sites and or start uploading crucial and personal information like name, password etc. Most malware uses predictable ways to download and upload files which are easy to locate and shut down. Whereas Conficker makes things way more complicated for finding and terminating its actions. According to antivirus firm F-secure this worn is programmed very complicated algorithm which in result generate hundreds of fake domain names such as abed.com,hturp.net etc. Out of which only one domain is used to download or upload data. Finding the site out of so many sites makes detection almost impossible procedure.
Alternatives
Interviewed by BBC, Kaspersky Lab's security analyst, Eddy Willems, said that a new strain of the worm was complicating matters.
"There was a new variant released less than two weeks ago and that's the one causing most of the problems," said Mr Willems
"The replication methods are quite good. It's using multiple mechanisms, including USB sticks, so if someone got an infection from one company and then takes his USB stick to another firm, it could infect that network too. It also downloads lots of content and creating new variants though this mechanism."
"Of course, the real problem is that people haven't patched their software," he mentioned.
According to Microsoft malware has infected millions of computers in almost of every parts of the world including in China, Brazil, Russia, and India having the highest number of victims.
Recommendations: We have good chances for protecting our computers by making sure that we update crucial security updates at any cost, and we use antivirus programs and keep its signature file updated for maximum protection.
Notebook Hardware Control and Monitoring Software
Posted by Muhammad | 2:24 AM | Hardware Test Utilities | 0 comments »Notebook hardware control and monitoring software is very neat utility for controlling hardware components on your notebook computers and it is free for personal use!
Using this utility you can:
- Monitor CPU clock, CPU load and CPU voltage
- Monitor CPU temperature and hard drive temperature
- Control CPU multiplier
- Control CPU warning and shutdown temperature
- Monitor hard drive SMART and temperature
- Monitor physical memory and virtual memory state
- Monitor battery status
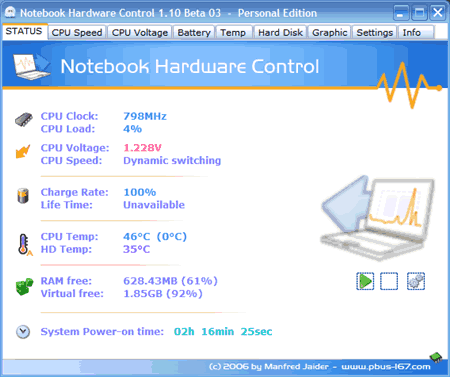
I just found this software and still testing it. You can download notebook hardware control utility here. Make sure to read the beginner’s guide.
Read More......Dissassembly Instructions for HP
Posted by Muhammad | 1:19 PM | Disassembly Instructions | 2 comments »Manuals for the following HP Pavilion Notebook PC series. Get maintenance and service guide.
HP Pavilion de2000, HP Pavilion dv1000, HP Pavilion dv2000, HP Pavilion dv4000, HP Pavilion dv5000, HP Pavilion dv6000, HP Pavilion dv8000m, HP Pavilion dv9000, HP Pavilion n Notebook PC series, HP Pavilion tx1000, HP Pavilion xf Notebook PC series, HP Pavilion xh Notebook PC series, HP Pavilion xt Notebook PC series, HP Pavilion xu Notebook PC series, HP Pavilion xz Notebook PC series, HP Pavilion zd7000, HP Pavilion zd8000, HP Pavilion ze1000, HP Pavilion ze2000, HP Pavilion ze4000, HP Pavilion ze5000, HP Pavilion zt1000, HP Pavilion zt3000, HP Pavilion zu1000, HP Pavilion zv5000, HP Pavilion zv6000, HP Pavilion zx5000
Manuals for the following HP Special Edition Notebook PCs. Get maintenance and service guide.
Special Edition L2000 CTO Notebook PC, Special Edition L2005A3, Special Edition L2005A4, Special Edition L2005CL, Special Edition L2005CM, Special Edition L2005CO, Special Edition L2005CU, Special Edition L2005CX, Special Edition L2005US, Special Edition L2098XX, Special Edition L2099XX, Special Edition L2105CA, Special Edition L2105CL, Special Edition L2105NR, Special Edition L2205NR, Special Edition L2300 CTO Notebook PC, Special Edition L2310CU
Dissassembly Instructions for Compaq
Posted by Muhammad | 1:14 PM | Disassembly Instructions | 0 comments »Fixing a HP/Compaq laptop yourself? Need some help with taking the laptop apart? Here are links to manuals with step-by-step disassembly instructions. All these manuals are available from the HP website.
Here’s how to get the manual:
1. Follow the link
2. Select your model
3. Go to manuals
4. Find the maintenance and service guide and open it up (pdf file, some of them are huge)
5. Go to Removal and Replacement procedures chapter, you’ll find disassembly instructions in there
Manuals for the following Compaq Armada Notebook PC series. Get maintenance and service guide.
Compaq Armada 110, Compaq Armada 110s, Compaq Armada 1100, Compaq Armada 1500, Compaq Armada 1500c, Compaq Armada 1700, Compaq Armada 1750, Compaq Armada 3500, Compaq Armada 4100, Compaq Armada 4200, Compaq Armada 6500, Armada 7300, Compaq rmada 7400, Compaq Armada 7700, Compaq Armada 7800, Compaq Armada e500, Compaq Armada e500s, Compaq Armada E700, Compaq Armada m300, Compaq Armada m700, Compaq Armada SB, Compaq Armada V300
Manuals for the following Compaq Evo Notebook PC series. Get maintenance and service guide.
Compaq Evo n150, Compaq Evo n160, Compaq Evo n180, Compaq Evo n400c, Compaq Evo n410c, Compaq Evo n600c, Compaq Evo n610c, Compaq Evo n610v, Compaq Evo n620c, Compaq Evo n800c, Compaq Evo n800v, Compaq Evo n800w, Compaq Evo n1000c, Compaq Evo n1000v, Compaq Evo n1005v, Compaq Evo n1010v, Compaq Evo n1015v, Compaq Evo n1020v, Compaq Evo n1050v, Compaq Evo n200, Compaq Evo n110, Compaq vo n115
Manuals for the following HP Compaq Notebook PC series. Get maintenance and service guide.
HP Compaq 2400, HP Compaq 4400, HP Compaq 6100, HP Compaq 6200, HP Compaq 6300, HP Compaq 6305, HP Compaq 7400, HP Compaq 8200, HP Compaq 8400, HP Compaq 9400, HP Compaq nc4000, HP Compaq nc4010, HP Compaq nc4200, HP Compaq nc6000, HP Compaq nc6400, HP Compaq nc8000, HP Compaq nw8000, HP Compaq nw8240, HP Compaq nx4300, HP Compaq nx4800, HP Compaq nx4820, HP Compaq nx5000, HP Compaq nx6130, HP Compaq nx7000, HP Compaq nx7010, HP Compaq nx7100, HP Compaq nx7200, HP Compaq nx7220, HP Compaq nx7300, HP Compaq nx9000, HP Compaq nx9005, HP Compaq nx9008, HP Compaq nx9010, HP Compaq nx9020, HP Compaq nx9030, HP Compaq nx9040, HP Compaq nx9100, HP Compaq nx9105, HP Compaq nx9110, HP Compaq nx9500, HP Compaq nx9500A, HP Compaq nx9600
Read More......Disclaimer: I’ve made these instructions only for people experienced with soldering and repairing computers. If you don’t feel comfortable doing this job, please do not open the laptop or you can permanently damage your computer. Take your laptop to a professional repair shop instead.
Use this repair guide at your own risk.
First of all, you’ll have to disassemble your laptop and remove the motherboard. Here you’ll find disassembly instructions for some major laptop brands such as IBM, Dell, HP, Compaq, Toshiba. If your laptop is not on the list, you’ll have to figure out yourself how to take it apart.
For this repair you’ll need the following tools.
1. Soldering iron or soldering station. I use Weller WES51 soldering station and for this job I set temperature to about 800-850°F.
2. I use high-tech rosin core silver-bearing solder from Radioshack with diameter 0.022″ ( Catalog #: 64-013 ). I think standard rosin core solder will work just fine.
3. Desoldering pump for removing solder around component leads. I use Edsyn Soldapullt pump, model DS 017.
4. 99% isopropyl alcohol and tooth brash for cleaning the motherboard from flux.
5. A new DC power jack, you can find a cheap one here.


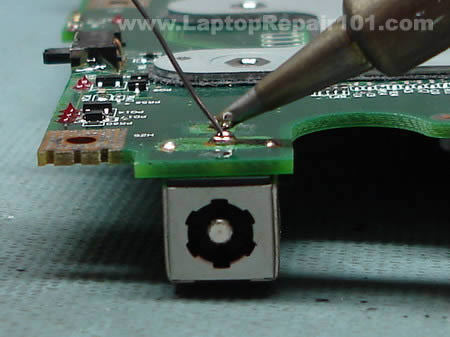
As you see on the following picture, the solder drop on the positive terminal looks different than on other three contacts. That’s where the problem is. The positive pin is not making a good contact with the motherboard and because of that power to the laptop cuts off when I move the power plug inside the power jack.
I’m going to desolder the power jack from the motherboard, clean contacts on both power jack and motherboard and then solder it back in place - this is the proper way fixing the power problem.
 power jack bottom
power jack bottom
DC power jack repair guide. Do-it-yourself instructions.
This guide will explain how to repair a failed or loose DC power jack on a laptop computer yourself. Here’s my previous post related to DC power jack related issues.
Disclaimer: I’ve made these instructions only for people experienced with soldering and repairing computers. If you don’t feel comfortable doing this job, please do not open the laptop or you can permanently damage your computer. Take your laptop to a professional repair shop instead.
Use this repair guide at your own risk. ![]()
First of all, you’ll have to disassemble your laptop and remove the motherboard. Here you’ll find disassembly instructions for some major laptop brands such as IBM, Dell, HP, Compaq, Toshiba. If your laptop is not on the list, you’ll have to figure out yourself how to take it apart.
For this repair you’ll need the following tools.
1. Soldering iron or soldering station. I use Weller WES51 soldering station and for this job I set temperature to about 800-850°F.
2. I use high-tech rosin core silver-bearing solder from Radioshack with diameter 0.022″ ( Catalog #: 64-013 ). I think standard rosin core solder will work just fine.
3. Desoldering pump for removing solder around component leads. I use Edsyn Soldapullt pump, model DS 017.
4. 99% isopropyl alcohol and tooth brash for cleaning the motherboard from flux.
5. A new DC power jack, you can find a cheap one here.

Laptop DC power jack repair guide.

As you see on the following picture, the solder drop on the positive terminal looks different than on other three contacts. That’s where the problem is. The positive pin is not making a good contact with the motherboard and because of that power to the laptop cuts off when I move the power plug inside the power jack.
I’m going to desolder the power jack from the motherboard, clean contacts on both power jack and motherboard and then solder it back in place - this is the proper way fixing the power problem.

Start desoldering process with adding some new fresh solder to all three contacts. This will make old solder more flowable, easier to remove.
While heating one of the contacts, remove the solder from this contact using the desoldering pump. Repeat the same steps with all power jack contacts until you remove as much solder as possible.
 The DC power jack is almost removed from the motherboard.
The DC power jack is almost removed from the motherboard.Be careful. Inside the positive hole there is a copper sleeve witch connects the terminal on one side of the motherboard with the traces on the other side. If you are removing the power jack with force, you can pull the sleeve from the hole. You don’t want to do that.
So, do not apply any force and make sure the solder is melted when you are removing the power jack. I hope you understand what I’m talking about.

After the power jack is removed, clean all oxidized contacts with a knife.
 Apply a fresh coat of solder to all contacts on the power jack.
Apply a fresh coat of solder to all contacts on the power jack. You can remove the flux using the tooth brash and alcohol. It’s not necessary but it will make your job looking clean.
You can remove the flux using the tooth brash and alcohol. It’s not necessary but it will make your job looking clean. Apply a fresh coat of solder to all power jack terminals on both sides of the motherboard.
Apply a fresh coat of solder to all power jack terminals on both sides of the motherboard.This side has been coated.

And this side has been coated too.

Now you can install the power jack back on the motherboard. Put something under power jack so there is no gap between the jack and the motherboard. Now you are ready to solder the jack back in place.
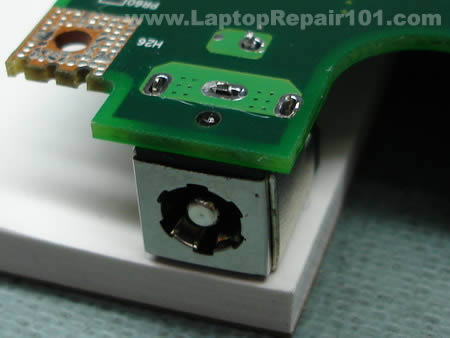
Solder all power jack pins.

The job is done and the laptop DC power jack is fixed. B-E-A-utiful!
Now just install the motherboard back into the laptop and you are done.

How to delete temporary files and directories (Win 95-XP)
Posted by Muhammad | 10:04 AM | Computer Troubleshooting, Laptop Troubleshooting, Performance Boosting | 0 comments »- Close all open programs.
- Click Start , select Programs , select Accessories , select System Tools , and then click Disk Cleanup (see Figure 1).
- When prompted, select the name of a drive from the drop-down list. (Drive C:\ is normally the hard drive on a PC. However it may be both drive C:\ and drive D:\ if there are multiple hard drives, or if hard drive is configured for multiple logical drives.)
- Place a check next to the types of files to be deleted. It is always safe to delete temporary files, Internet files, and recycle bin files.
- Select OK to begin the cleanup. When prompted, click Yes to confirm the actions.Figure 1: Disk Cleanup Window

| WARNING: Running these commands incorrectly may delete important files and could cause the computer to stop working. Do not perform these activities if you are not experienced using these commands. |
Use antivirus to remove spyware and adware
Posted by Muhammad | 2:32 AM | Antivirus, Computer Troubleshooting, Laptop Troubleshooting | 0 comments »
Use an antivirus program to remove spyware and adware
Adware is any program that displays advertising banners while it is running. This may include sometimes annoying pop-up windows. Spyware is any application that collects information from the computer and sends that information to another computer over the Internet.
These programs, as well as viruses and worms, can degrade the system resources. Set up a schedule to search for and remove these types of programs.
Install an antivirus and antispyware software and use the automatic update feature to keep the virus and spyware definition files current. Use the Symantec Security Check to test the computer's exposure to a wide range of online threats. It's a free service designed to help HP customers determine their Internet security needs.
Resources
Paid solutions are often better than the free ones. Here is a list of paid solutions.
http://www.symantec.com
Symantec's antivirus products have historically always provided excellent detection and removal of malware. On the downside, that protection came at the price of often crippling system performance. That's now a thing of the past. Performance overhauls are the hallmark of Norton Internet Security 2009, which features 'pulse updates' to deliver more frequent and thus smaller signature updates, whitelisting to streamline scan times, and a lighter, sleeker footprint that installs in mere minutes.
Avira AntiVir PersonalEdition PremiumAntiVir is a consistent leader in independent antivirus tests. Avira's AntiVir PersonalEdition Premium is a low-impact, easy to use virus scanner that also the ability to make an antivirus rescue CD for your system. Also includes WebGuard to protect against malicious or compromised websites. Five euros of each purchase is automatically donated to the Auerbach Foundation, a non-profit that supports various charity and community-related services. AntiVir PersonalEdition Premium should be used in conjunction with a firewall.
McAfee VirusScan Plus
McAfee VirusScan Plus is an ideal candidate for those seeking an antivirus/firewall combination without all the bloat of traditional Internet security suites. McAfee VirusScan Plus makes an easy job of removing adware and spyware, something not all antivirus products deliver. SiteAdvisor service is including, helping to guard against malicious websites. Kaspersky Anti-Virus Personal
Kaspersky Anti-Virus Personal offers excellent antivirus protection, perhaps unsurpassed in its ability to unpack and scan compressed files - something that trips up a lot of other vendors. Should be used in conjunction with a firewall.5. Panda Antivirus Pro 2009
Panda Antivirus Pro 2009 combines antivirus, antispyware, antiphishing and a firewall with its highly touted behavior-based TruPrevent Technology. License covers use on up to three computers and includes free tech support via email (telephone support options are also available).6. BitDefender Antivirus Plus
Softwin's BitDefender Professional protects against viruses, spyware, and instant messaging threats, as well as offering firewall rules to block undesirable traffic and a privacy gateway to keep your identity and preferences private while surfing the Internet.7. Eset Nod32
Nod32 features a small footprint, low performance hit, and fast scan speeds, providing focused virus protection ideal for gamers or those with an older PC. Should be used in conjunction with a firewall.8. AVG Anti-Malware
AVG Anti-Malware combines traditional virus protection with adware and spyware scanning, in a low impact footprint ideal for resource-strained PCs or those who just want the best performance possible out of their computers. Free tech support is available via email and the standard license includes two years of protection. Should be used in conjunction with a firewall.9. G Data AntiVirusKit (AVK)
AntiVirusKit (AVK) provides a double layer of protection, bundling two of the best antivirus engines - Kaspersky and BitDefender - under a single, easy-to-use console. You'll want to bolster G Data's AVK with a firewall.10. F-PROT Antivirus
F-PROT Antivirus for Windows offers a feature that's increasingly harder to find - it includes a command-line scanner that can be used to create a rescue CD for scanning the system in Safe Mode. This is a particularly effective way to remove stubborn resuscitators. Firewall not included.
Boost Your PC and Notebook's Performance!
Posted by Muhammad | 2:09 AM | Computer Troubleshooting, Laptop Troubleshooting, Performance Boosting | 0 comments »

Here are some simple and advanced tips and tricks to improve your PC's/Notebook's performance. Follow these techniques, and see the results!
This tutorial is valid for : All brands of PCs and Notebooks with Operating System: Windows only.
BASIC Techniques
ADVANCED Techniques
Conficker: Protect Yourself! Win32/Conficker.C Virus Triggers April 1st, 2009
Posted by Muhammad | 10:17 AM | Antivirus, Top Threats | 2 comments »Win32/Conficker.C Virus Triggers April 1st, 2009.
Conficker, also know as Downup, Downadup and Downadup is a computer worm that exploits a known vulnerability in the Windows Server System installed in Windows 2000, XP, Server 2003, and Server 2008.
Symptoms of infection:
- Account lockout policies are automatically reset.
- Microsoft Windows Services, such as Background Intelligent Transfer Service, Windows Defender, and Error Reporting Services are automatically Disabled.
- Domain controllers respond very slowly to their client requests.
- System networks usually get congested. This can be checked by network traffic chart on the windows task manager.
- Windows systems updates cannot be accessed.
- Launches a brute force dictionary attack against administrator passwords to help it spread through ADMIN$
Experts say that this is the WORST attacker after SQL Spammer. In recent years, a range of 9 - 15 million computers across the globe were infected by this worm.
Patching and Removal
On 15 October 2008 Microsoft released a patch (MS08-067) to fix the vulnerability.[30] Removal tools are available from Microsoft,[31] BitDefender,[32] ESET, Symantec,[33] Sophos,[34] and Kaspersky Lab,[35] while McAfee and AVG can remove it with an on-demand scan.[36][37] While Microsoft has released patches for the later Windows XP Service Packs 2 and 3 and Windows 2000 SP4 and Vista, it has not released any patch for Windows XP Service Pack 1 or earlier versions (excluding Windows 2000 SP4), as the support period for these service packs has expired. Since the virus can spread via USB drives that trigger AutoRun, disabling the AutoRun feature for external media (through modifying the Windows Registry) is recommended.[38] However the United States Computer Emergency Readiness Team describe Microsoft's guidelines on disabling Autorun as being "not fully effective," and they provide their own guides.[39] Microsoft has released a removal guide for the worm via the Microsoft website.
Also, on March 16, 2009, BitDefender released an updated tool to remove the already famous Downadup/Conficker worm on a new domain that has not been blocked by the malicious computer code at a website called "bdtools.net".
Apart from the fact that the BitDefender tool removes the latest and most resilient to disinfection release of the virus, it also comes as a separate installer dedicated to network administrators. In this way, the scanner can be dispatched throughout networks in order to remotely scan and disinfect workstations.
Read More......
TShoots: How to Optimize the Notebook's Battrey Life?
Posted by Muhammad | 1:50 AM | Battery Optimization, Computer Troubleshooting, Laptop Troubleshooting | 1 comments »- It is not uncommon for a notebook battery to last less than an hour or over two hours. The approximate battery life for a NiMH battery is between 1.5 and 2.5 hours and for a lithium ion (Li ion) battery between 2.0 and 3.0 hours. So don't worry if it doesn't last for more time than that.
- Do NOT plug the AC adapter when the laptop/notebook is not in use. Simply plug the AC adapter off.
- To optimize the battery life and improve its performance, fully discharge and recharge the battery at least once in every 60 days.
- With out the AC power the Notebook will work with the battery and the maximum time for battery is 2 to 2 1/2 hrs. You can use the Notebook continiously without of shutdown for 5 - 6 hrs. A shutdown is required after this.
- If you have to replace the battery, Always follow the vendor's recommendation. Do not experiment with your battery.
- To optimize the battery life, always use lower than full screen resolution on your notebook. High resolutions call for high power, which inturn, adversly affect the life of your battery.
- Do NOT overcharge the battery. Once the battery is fully charged, disconnect it from the AC adapter. This will prevent overheating.
- Windows Vista comes with a default power meter gadget. If you're running windows XP/XP Professional or XP home edition, you can download and install the Power Meter Gadget after downloading and installing Google Desktop from
- If you have bluetooth or infrared on your notebook, turn it off at times when you don't need it. Both IR ad Bluetooth consume lots of energy, generally affecting the overall lifetime of your notebook's battery.
- With Windows Vista, always set the power management options from the control panel.
- If you're not going to be using your notebook for 2 weeks or over 2 weeks, you need to
1. Remove the AC adapter.
2. Remove the battery pack
3. Seperately store the battery in a cool, dry place.
Read More......














